How HTTPS exposed the person who put information about me online
On the 10th of February, my latest grades and comments from teachers about me (and other students) were accidentally emailed to the wrong persons. A sudden change in the mailing-list, that the teachers used, caused the email to be sent to all students. This included the students from the two other schools that are part of the Tabor College educational institution.
In this era of the digitally aware youth, the news spread very fast and before any action could be taken the information was spread to other individuals outside of the three schools. Staff quickly asked students to remove the data from their email accounts (part of GSuite). Things looked normal, parents were informed, the system operators were trying to find the point of failure that caused the mailing list to malfunction and Tabor College stated publicly that they were trying to do everything in their power to find anyone who might have spread the information outside of Tabor College.
It was only a few days later when I read in the local newspaper that they had found a website hosting the ‘leaked’ documents. They did not name the website, but they stated very clearly that they had taken down the website through the web hosting provider.
Nothing bad had happened (yet), I got a few messages from friends who had seen my grades and comments about me. Some people had received mean comments, but all of them could cope with it.
Two weeks passed when I suddenly ran across some interesting Google search results leading me to a new website hosting the leaked documents, including the letter from the staff to the student's parents and some (recently updated) news articles.
My first thought was, “I need to get this website offline immediately” but then I realised I should probably warn the staff, so I got in touch with one of the system operators and had a nice chat with him about this website. To take a website down you either have to contact the web hosting provider or the owner of the website. To do so one would look in the WHOIS registry to find information that can be used to contact either of them. This is where it gets painful, the WHOIS registry of ‘.nl’ domain names (managed by the SIDN) does not give away a lot of data in contrast to a ‘.com’ domain (if you do not use some sort of a privacy protection company).
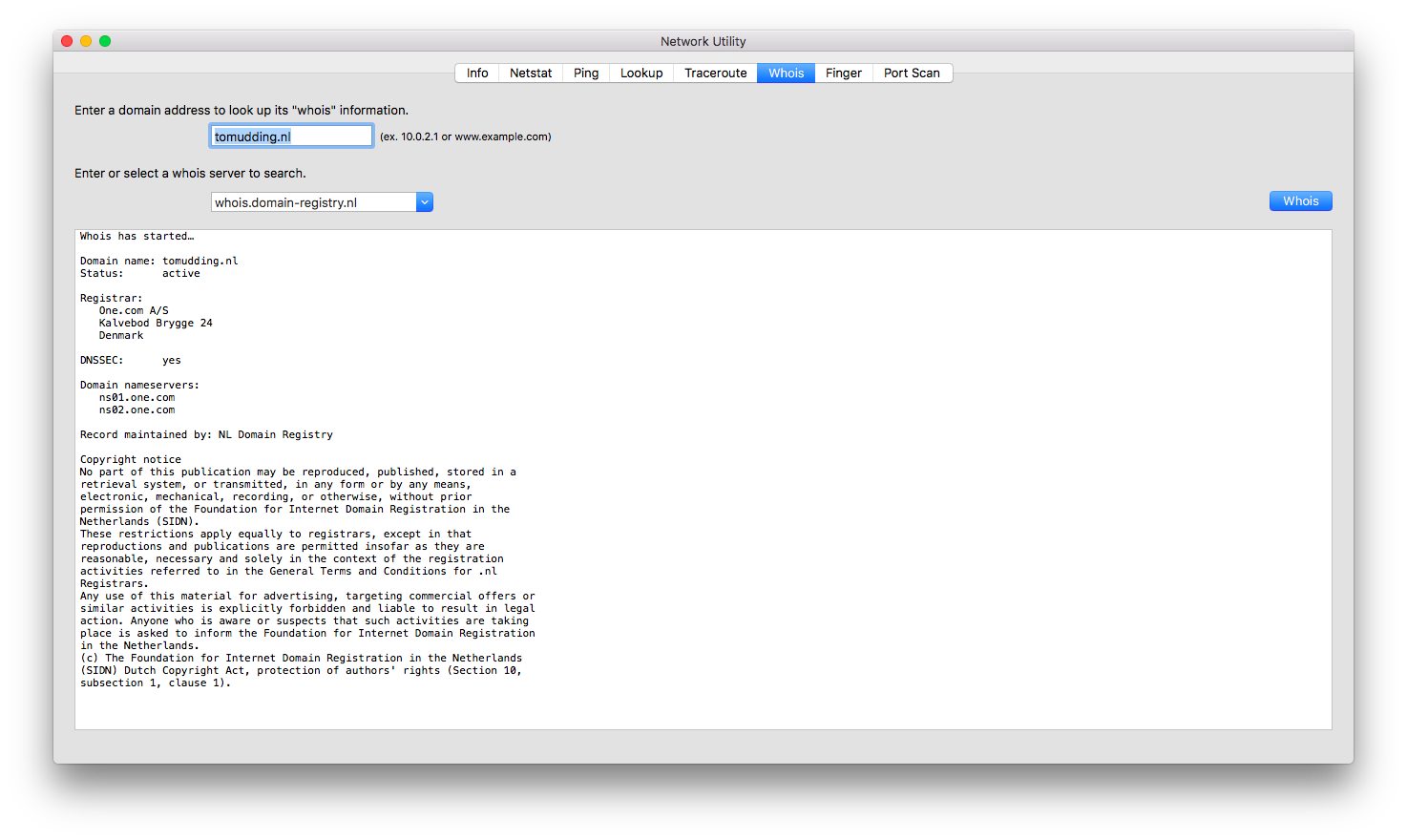
WHOIS request of tomudding.nl
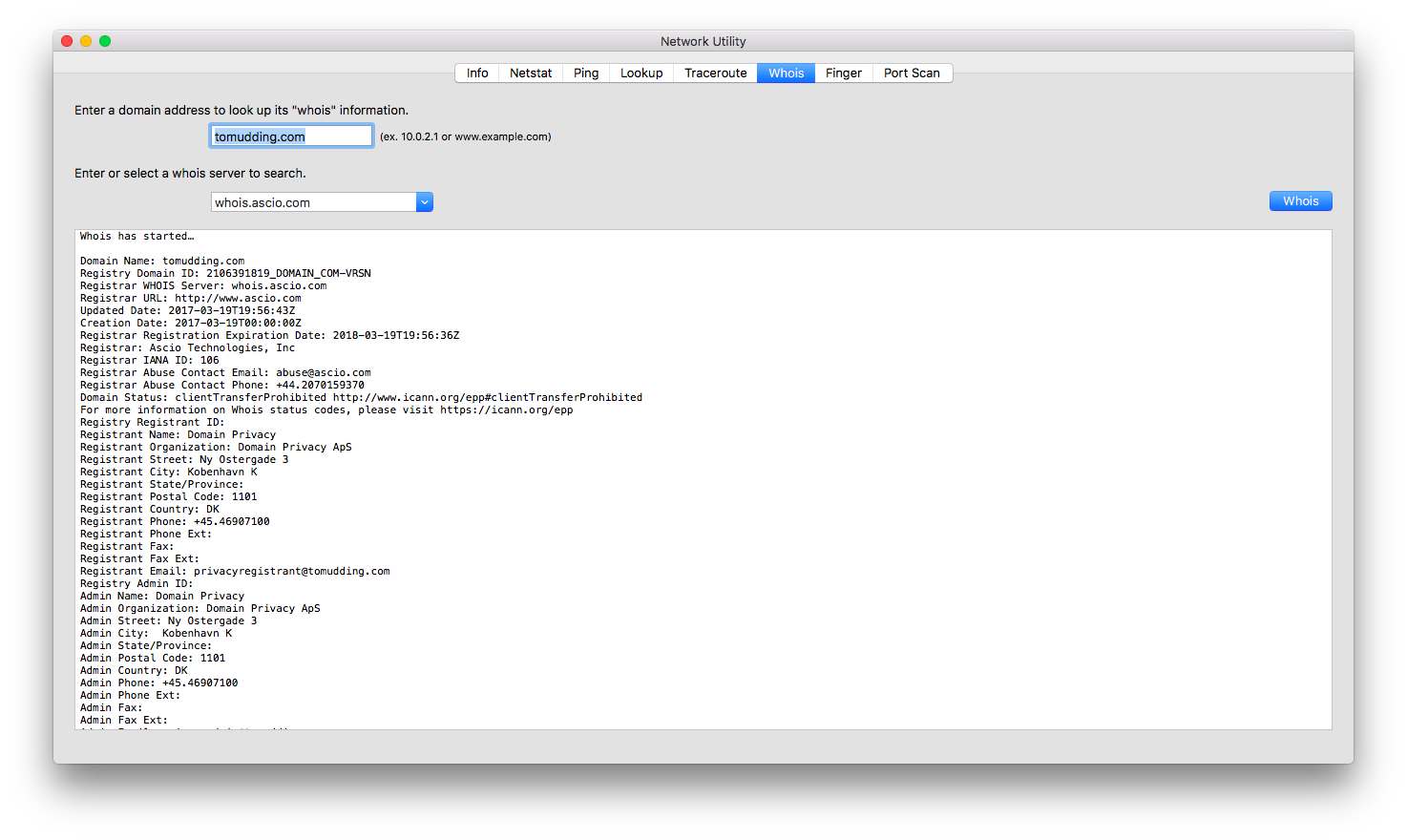
WHOIS request of tomudding.com (with privacy protection)
The results yielded from retrieving the WHOIS information were unfavourable, only a contact address for the web hosting provider and a weird looking ‘hotmail.nl’ email address, which probably belonged to the owner of the website. The web hosting provider could only be contacted by emailing them and that would take a lot of time, so I focused on finding the owner of the website.
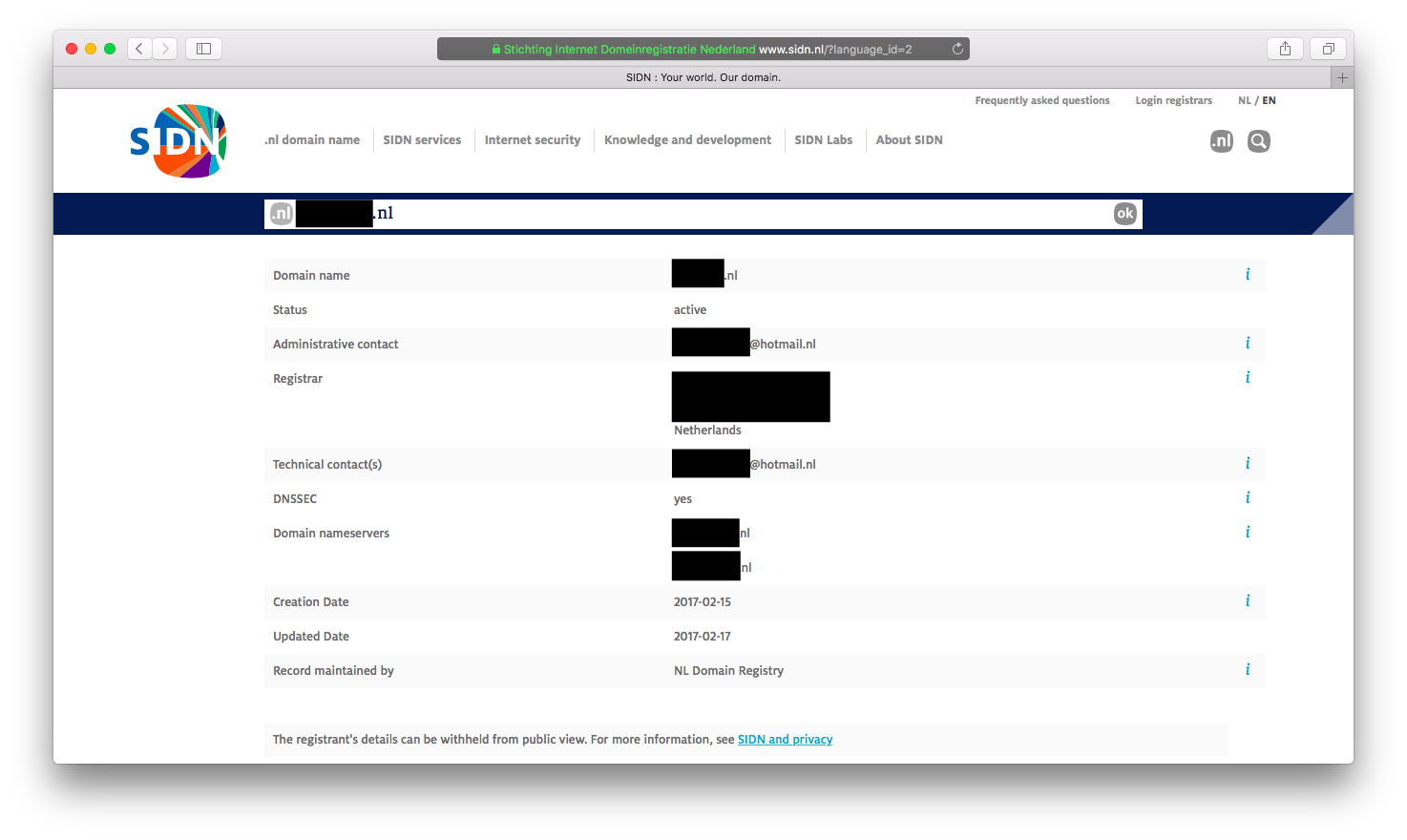
WHOIS request of the domain that hosts the files
Putting the email address into the Hotmail account recovery tool is not difficult and can always give you some information (If you are lucky). I was quite surprised that the recovery options contained both the last 2 digits of the mobile phone number and the first two characters of another email address, but both again a dead end.
So I started to put the email address I found in a reverse WHOIS search and no results came back. So I checked if there were records of other websites hosted on the same server as the website, I always use YouGetSignal becuase it is quite easy to use and up-to-date to a certain extent. Again no results and thus another dead end.
After a little less than 30 minutes I started to poke the web server where the website was hosted on. Checking if someone might have left a port open, any outdated software was used and eventually if it used a TLS certificate. It may sound weird but if you are hosting ‘sensitive’ information about me you have to use some form of encryption and finally, I had a lead.
Not wanting to leave my beloved Terminal window (which I had used to poke the server) I used OpenSSL to retrieve and verify the certificate.
openssl s_client -connect *****.nl:443Quite surprised I saw that there was another Common Name listed. This CN was clearly not the domain name I was looking for, but it provided me (after visiting the website) with all kinds of information about the owner of the .nl domain. The last two digits of the phone number were the same as those that I had found earlier, the address of this person was displayed and some other very personal information could be found.
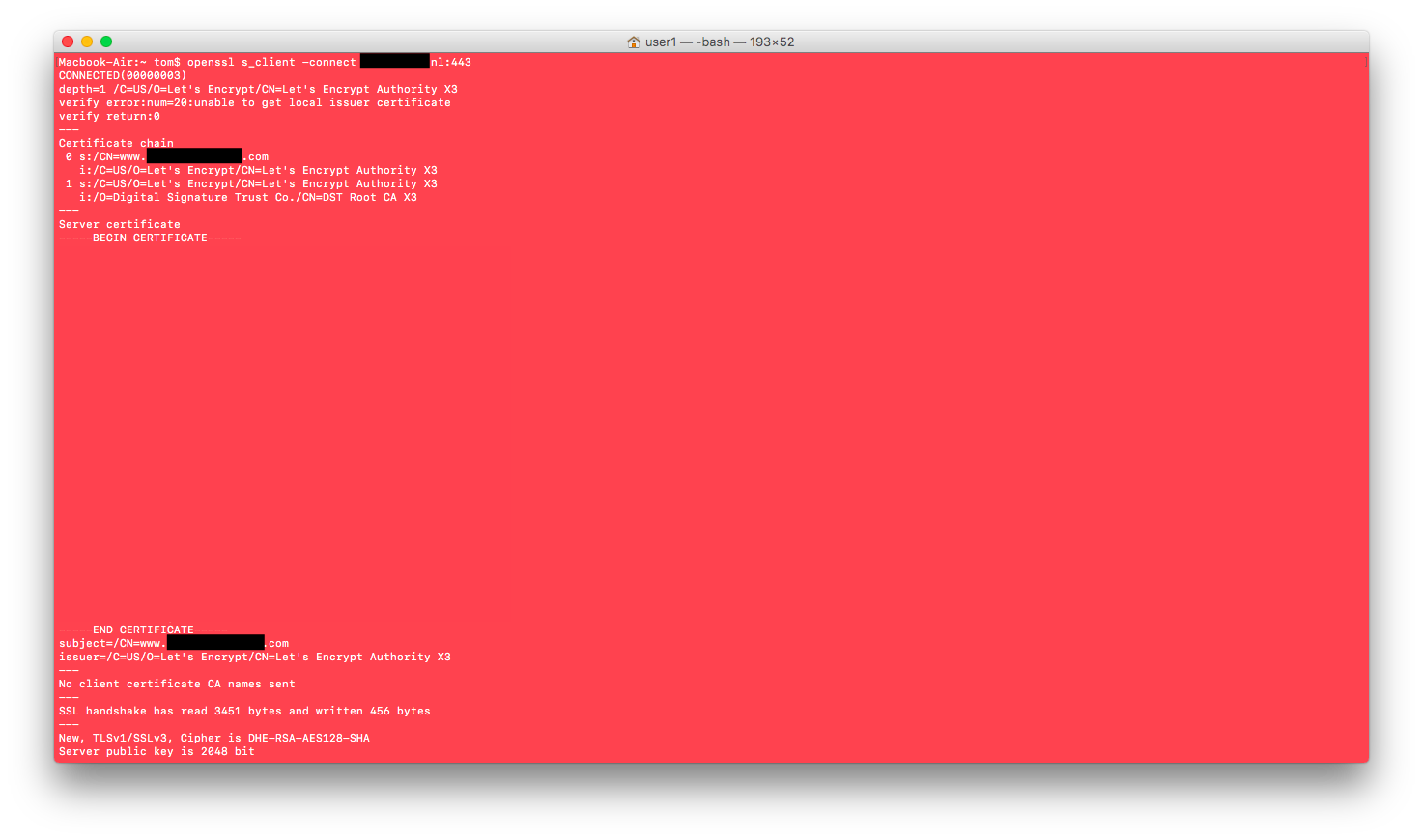
Output of the OpenSSL certificate check
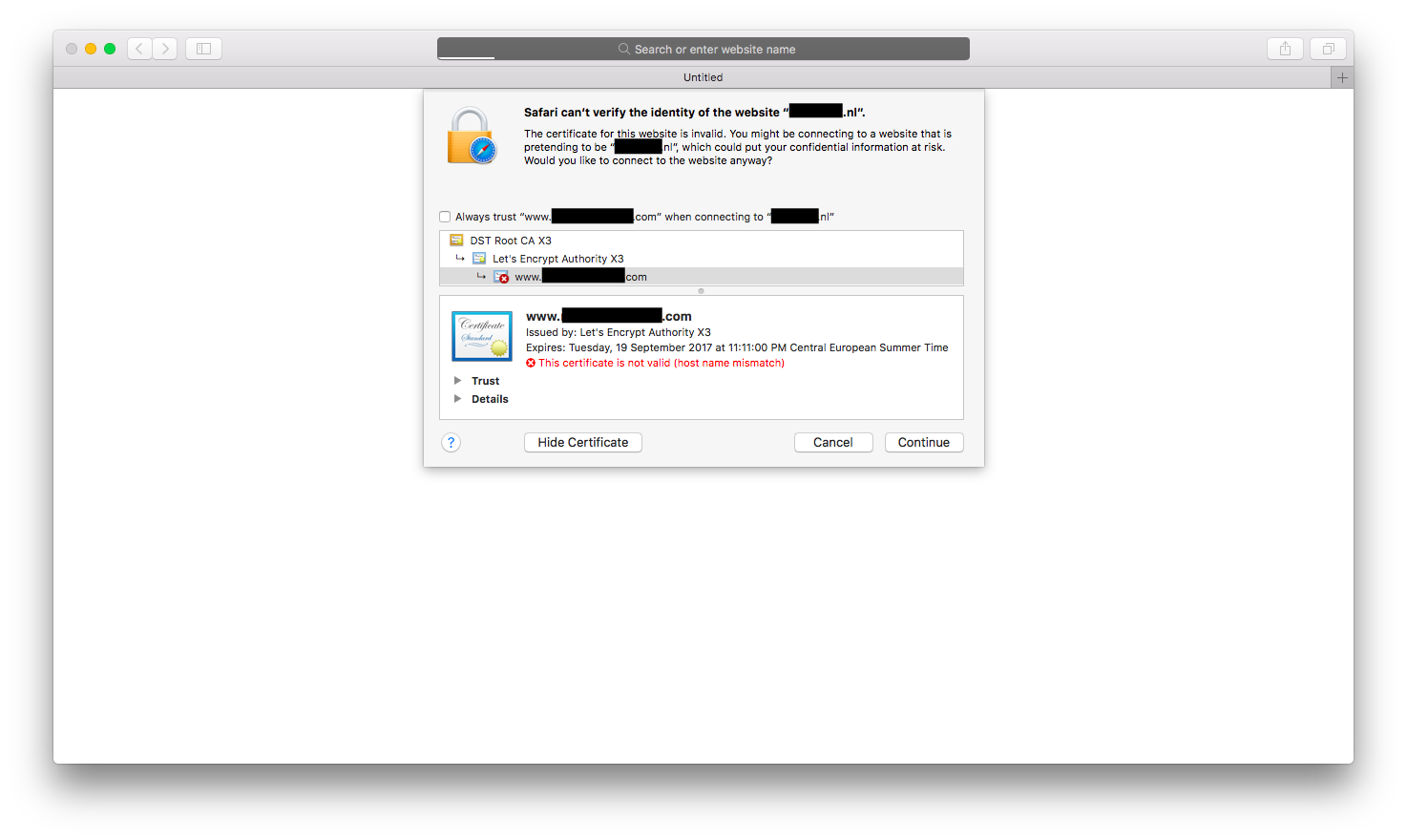
Hostname mismatch warning produced by Safari
After looking around for a bit I reported my findings to the system operator and eventually to the director. They managed to talk to the owner of the website and after that, the owner took the main page offline. Note the ‘main page’ because the documents are still on that server and you can still access them (if you happen to know the URL).
And that is how HTTPS exposed the person, who put information about me online.